Financial Data and Charitable Donors
Preliminary Estimates, T1 Family File
User's Guide
Table of contents
Charitable Donations (product #13C0014)
RRSP Contributors (product #17C0006)
Canadian Investors (product #17C0007)
Canadian Investment Income (product #17C0008)
Canadian Savers (product #17C0009)
Canadian Taxfilers (product #17C0010)
RRSP Contribution Limits (ROOM) (product # 17C0011)
Canadian Capital Gains (product #17C0012)
Data Source
Data Frequency
Data Quality
Confidentiality and Rounding
Glossary of Terms
Statistical Tables - Footnotes and Historical Availability
Geography
Geographic Levels – Postal Geography
- Adding Postal Areas Without Duplication
- City identification number (CityID)
- Hierarchy of postal geography
Geographic Levels – Census Geography
Geographic Levels – Special Geography
We Invite Your Comments
List of available data products
Income Statistics Division
Statistics Canada
income@statcan.gc.ca
February 2015
Data Source
The financial and donors databanks are derived from income tax returns. For the most part, tax returns were filed in the spring of the year following the reference year. For example, for the 2013 tax year, most income tax returns were filed by April 30, 2014.
Demographic characteristics such as age are given as of December 31 of the tax year. Income information is for the calendar year under review.
The data for the products associated with this release are derived from an early version of a file that Statistics Canada receives from Canada Revenue Agency (CRA). The file benefits from timeliness, but loses some accuracy because of it. This earlier tax file, often referred to as the T1 preliminary file, contains about 97% of the records on the CRA file received four to five months later.
Data Frequency
Data are updated on an annual basis.
Data Quality
i) Number of Canadian taxfilers
The data used are direct counts from T1 preliminary tax file. For the 2013 tax year, 25.5 million Canadians or 71.9% filed tax returns.
| Tax year | Number of Taxfilers ('000) | Date of Population Estimate | Population ('000) | Coverage (%) |
|---|---|---|---|---|
| 1991 | 18,786 | 01-Apr-92 | 28,270 | 66.5% |
| 1992 | 19,267 | 01-Apr-93 | 28,601 | 67.4% |
| 1993 | 19,882 | 01-Apr-94 | 28,907 | 68.8% |
| 1994 | 20,184 | 01-Apr-95 | 29,212 | 69.1% |
| 1995 | 20,536 | 01-Apr-96 | 29,514 | 69.6% |
| 1996 | 20,772 | 01-Apr-97 | 29,818 | 69.7% |
| 1997 | 21,113 | 01-Apr-98 | 30,080 | 70.2% |
| 1998 | 21,431 | 01-Apr-99 | 30,315 | 70.7% |
| 1999 | 21,893 | 01-Apr-00 | 30,594 | 71.6% |
| 2000 | 22,249 | 01-Apr-01 | 30,911 | 72.0% |
| 2001 | 22,804 | 01-Apr-02 | 31,252 | 73.0% |
| 2002 | 22,968 | 01-Apr-03 | 31,548 | 72.8% |
| 2003 | 23,268 | 01-Apr-04 | 31,846 | 73.1% |
| 2004 | 23,625 | 01-Apr-05 | 32,143 | 73.5% |
| 2005 | 23,952 | 01-Apr-06 | 32,471 | 73.8% |
| 2006 | 24,258 | 01-Apr-07 | 32,818 | 73.9% |
| 2007 | 24,624 | 01-Apr-08 | 33,191 | 74.2% |
| 2008 | 24,987 | 01-Apr-09 | 33,604 | 74.4% |
| 2009Note 1 | 24,321 | 01-Apr-10 | 34,002 | 71.5% |
| 2010Note 1 | 24,495 | 01-Apr-11 | 34,368 | 71.3% |
| 2011Note 1 | 24,842 | 01-Apr-12 | 34,754 | 71.5% |
| 2012Note 1 | 25,160 | 01-Apr-13 | 35,025 | 71.8% |
| 2013Note 1 | 25,483 | 01-Apr-14 | 35,416 | 71.9% |
|
||||
ii) Elderly population
Some elderly Canadians receiving only Old Age Security and Guaranteed Income Supplement do not file because they have low or no taxable income. However, with the introduction of the Federal Sales Tax (FST) Credit in 1986 and the Goods and Services Tax (GST) Credit in 1990, the percentage of the elderly population filing tax returns has increased.
iii) Low Income
Persons below a certain level of income with low income have no tax liability and are not required to file tax returns. However, with the introduction of the Child Tax Credit in 1978, the Federal Sales Tax (FST) Credit in 1986, the Goods and Services Tax (GST) Credit in 1990, and the Child Tax Benefits in 1993, persons with low income are still likely to file tax returns in order to apply for these credits.
Confidentiality and Rounding
Over the years since its creation, the T1 Family File (T1FF) has become known as a reliable, annual source for income and demographic estimates. To protect the confidentiality of Canadians, all data are subject to the confidentiality procedures of rounding and suppression.
All counts are rounded. Rounding may increase, decrease, or cause no change to counts. Rounding can affect the results obtained from calculations. For example, when calculating percentages from rounded data, results may be distorted as both the numerator and denominator have been rounded. The distortion can be greatest with small numbers.
All reported amounts are rounded to the nearest $5,000 dollars.
Since 1990, data cells represent counts of 15 or greater, and are rounded to a base of 10. For example, a cell count of 15 would be rounded to 20 and a cell count of 24 would be rounded to 20.
Note: Counts represent the number of persons. Reported amounts are aggregate dollar amounts reported.
In the data tables:
Medians, Percentiles and Average amount are rounded to the nearest ten dollars.
Percentages are published with no decimal and calculated on rounded data; therefore, the sum of percentages might not equal 100% in the case of small counts.
Suppressed Data
To maintain confidentiality, data cells have been suppressed whenever:
- areas comprise less than 100 taxfilers;
- cells represent less than 15 taxfilers;
- cells were dominated by a single filer;
Suppressed data may occur:
i) Within one area:
- when one of the income categories is suppressed, a second category must also be suppressed to avoid disclosure of confidential data by subtraction (called residual disclosure);
- when one of the gender categories is suppressed, the other gender category must also be suppressed to avoid residual disclosure;
- when one age group category is suppressed, another age group must also be suppressed to avoid residual disclosure.
ii) Between areas:
- when a variable amount in one area is suppressed, that variable amount is also suppressed in another area to prevent disclosure by subtraction.
RRSP Contributors (product #17C0006)
This databank provides information on taxfilers who contributed to a Registered Retirement Savings Plan (RRSP) during the tax year under review.
The content of the databank is as follows:
Table 1: Summary
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Number of RRSP contributors
Column 8 – Average age of RRSP contributors
Column 9 – Median employment income of RRSP contributors
Column 10 – 75th percentile of employment income of RRSP contributors
Column 11 – Amount of RRSP dollars reported (in thousands of dollars)
Column 12 – Median RRSP contribution
Table 2: Age groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of RRSP contributors
Column 8 – Percent of contributors 0 to 24 years of age
Column 9 – Percent of contributors 25 to 34 years of age
Column 10 – Percent of contributors 35 to 44 years of age
Column 11 – Percent of contributors 45 to 54 years of age
Column 12 – Percent of contributors 55 to 64 years of age
Column 13 – Percent of contributors 65+ years of age
Column 14 – Total amount of RRSP dollars reported (in thousands of dollars)
Column 15 – Percent of contributions reported by age group 0 to 24
Column 16 – Percent of contributions reported by age group 25 to 34
Column 17 – Percent of contributions reported by age group 35 to 44
Column 18 – Percent of contributions reported by age group 45 to 54
Column 19 – Percent of contributions reported by age group 55 to 64
Column 20 – Percent of contributions reported by age group 65+
Table 3: Sex
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Percent of taxfilers who are male
Column 8 – Percent of taxfilers who are female
Column 9 – Total number of RRSP Contributors
Column 10 – Percent of contributors who are male
Column 11 – Percent of contributors who are female
Column 12 – Total amount of RRSP dollars reported (in thousands of dollars)
Column 13 – Percent of contributions reported by males
Column 14 – Percent of contributions reported by females
Column 15 – Median RRSP contribution of all contributors
Column 16 – Median RRSP contribution of males
Column 17 – Median RRSP contribution of females
Table 4: Income groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of RRSP contributors
Column 8 – Percent of RRSP contributors with total income less than $20,000
Column 9 – Percent of RRSP contributors with total income between $20,000 and $39,999
Column 10 – Percent of RRSP contributors with total income between $40,000 and $59,999
Column 11 – Percent of RRSP contributors with total income between $60,000 and $79,999
Column 12 – Percent of RRSP contributors with total income $80,000+
Column 13 – Total amount of RRSP dollars reported (in thousands of dollars)
Column 14 – Percent of total RRSP amount reported by contributors with total income less than $20,000
Column 15 – Percent of total RRSP amount reported by contributors with total income between $20,000 and $39,999
Column 16 – Percent of total RRSP amount reported by contributors with total income between $40,000 and $59,999
Column 17 – Percent of total RRSP amount reported by contributors with total income between $60,000 and $79,999
Column 18 – Percent of total RRSP amount reported by contributors with total income $80,000+
RRSP Contribution Limits (ROOM) (product # 17C0011)
The Registered Retirement Savings Plan (RRSP) Room databank was created to provide information on the RRSP contribution limit (RRSP Room) available. This product can be used in conjunction with the RRSP databank which concentrates on the RRSP contributors.
In 1989, the legislation dictated that contribution limits for persons not contributing to a registered pension plan (RPP) or a Deferred Profit Sharing Plan (DPSP) was 20% of earned income to a maximum of $7,500. The limit for RPP and DPSP members was 20% of earned income to a maximum of $3,500 less the amount contributed by the employee to the RPP or DPSP.
Further amendments to the Income Tax Act relative to RRSPs, taking effect January 1, 1991, were intended to make RRSP contribution limits more equitable. The RRSP contribution limit was set at 18% of earned income for the previous tax year, to a set maximum minus the Pension Adjustment (PA). The PA represents the calculated value of the pension accrued through an RPP or a DPSP in the previous tax year.
Total RRSP Room represents the deduction limit that Canadians can claim with respect to contributions made to RRSPs. It does not include income eligible for transfers, such as retiring allowances and severance pay that may be rolled over into RRSPs. The sum of the deduction limit and rollovers represents the maximum amount that can be claimed as a deduction on line 208 of the income tax return.
| Earned income in tax year |
New room | Unused room | Total room (for tax year+1) |
|---|---|---|---|
| 1991 | For 1992 | pre1991 = 0 | New room only |
| 1992 | For 1993 | 1991 to 1992 | Unused room + new room |
| 1993 | For 1994 | 1991 to 1993 | Unused room + new room |
| 1994 | For 1995 | 1991 to 1994 | Unused room + new room |
| 1995 | For 1996 | 1991 to 1995 | Unused room + new room |
| 1996 | For 1997 | 1991 to 1996 | Unused room + new room |
| 1997 | For 1998 | 1991 to 1997 | Unused room + new room |
| 1998 | For 1999 | 1991 to 1998 | Unused room + new room |
| 1999 | For 2000 | 1991 to 1999 | Unused room + new room |
| 2000 | For 2001 | 1991 to 2000 | Unused room + new room |
| 2001 | For 2002 | 1991 to 2001 | Unused room + new room |
| 2002 | For 2003 | 1991 to 2002 | Unused room + new room |
| 2003 | For 2004 | 1991 to 2003 | Unused room + new room |
| 2004 | For 2005 | 1991 to 2004 | Unused room + new room |
| 2005 | For 2006 | 1991 to 2005 | Unused room + new room |
| 2006 | For 2007 | 1991 to 2006 | Unused room + new room |
| 2007 | For 2008 | 1991 to 2007 | Unused room + new room |
| 2008 | For 2009 | 1991 to 2008 | Unused room + new room |
| 2009 | For 2010 | 1991 to 2009 | Unused room + new room |
| 2010 | For 2011 | 1991 to 2010 | Unused room + new room |
| 2011 | For 2012 | 1991 to 2011 | Unused room + new room |
| 2012 | For 2013 | 1991 to 2012 | Unused room + new room |
| 2013 | For 2014 | 1991 to 2013 | Unused room + new room |
Calculation of contribution limits
For 1990, maximum contributions are:
- for non-participants in RPPs and DPSPs, the lesser of 20% of earned income and $7,500
- for participants in RPPs and DPSPs, 20% of earned income to a maximum of $3,500; the maximum is reduced according to employee contributions to RPPs/DPSPs.
For 1991 to 2013:
New room = 18% of earned income - PA - PSPA
Percentage of earned income to a maximum of
- $11,500 for 1991
- $12,500 for 1992 and 1993
- $13,500 for 1994
- $14,500 for 1995
- $13,500 for 1996
- $13,500 for 1997
- $13,500 for 1998
- $13,500 for 1999
- $13,500 for 2000
- $13,500 for 2001
- $13,500 for 2002
- $14,500 for 2003
- $15,500 for 2004
- $16,500 for 2005
- $18,000 for 2006
- $19,000 for 2007
- $20,000 for 2008
- $21,000 for 2009
- $22,000 for 2010
- $22,450 for 2011
- $22,970 for 2012
- $23,820 for 2013
Where PA = Pension Adjustment, and PSPA = Past Service Pension Adjustment
Prior to tax year 2000 (Room 2001):
Total Room (for tax year+1) = Unused Room (from 1991 forward) + New Room
For tax years 2000 to 2013 (Room 2001 to Room 2014):
Total Room (for tax year+1) = Unused Room accumulated since 1991 + (18% of earned income – Pension adjustment) – Current tax year contributions excluding rollovers
Data source for RRSP Room
Prior to the release of data for tax year 2000, the RRSP ROOM data were derived from a file received annually from the Canada Revenue Agency (CRA, formerly Canada Customs and Revenue Agency). CRA generated the data from an administrative system designed in response to changes to the Income Tax Act with respect to Registered Retirement Savings Plans, changes that took effect January 1, 1991.
The system records information for each taxfiler with "earned income" (income used to determine the RRSP deduction limit). The information includes each year's earned income, new room amounts and unused room amounts carried forward.
Starting with the 2001 ROOM (2000 tax data), the amount of RRSP Room is calculated from other variables on the preliminary file, variables which were previously unavailable.
This year's release of the RRSP Room data is based on 2013 income tax returns. Contributions towards these limits can be made up to February 2015, to be reported on the 2014 tax returns. The mailing address at the time of filing is the basis for the geographic information in the tables.
The content of the databank is as follows:
Table 1: Persons with room
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk number (no longer available)
Column 4 – Level of geography (see Geography section)
Column 5 – Place name
Column 6 – Amount of Room dollars reported (in thousands of $)
Column 7 – Amount of Unused Room dollars reported (in thousands of $)
Column 8 – Amount of New Room dollars reported (in thousands of $)
Column 9 – Number of taxfilers with Room
Column 10 – Number of taxfilers with Unused Room
Column 11 – Number of taxfilers with New Room
Table 2: Characteristics of persons with new room
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk number (no longer available)
Column 4 – Level of geography (see Geography section)
Column 5 – Place name
Column 6 – Number of taxfilers with New Room
Column 7 – Average Age of taxfilers with New Room
Column 8 – Percentage Female taxfilers with New Room
Column 9 – Median Earned Income of taxfilers with New Room
Column 10 – Average New Room
Column 11 – Percentage of taxfilers with New Room between $500 and $2,399
Column 12 – Percentage of taxfilers with New Room between $2,400 and $4,699
Column 13 – Percentage of taxfilers with New Room between $4,700 and $7,799
Column 14 – Percentage of taxfilers with New Room between $7,800 and $12,999
Column 15 – Percentage of taxfilers with New Room greater than $13,000
Additional notes for Table 2:
Column 11: The first value represents the 25th percentile and is recalculated periodically.
Column 12: The first value represents the 50th percentile and is recalculated periodically.
Column 13: The first value represents the 75th percentile and is recalculated periodically.
Column 14: The first value represents the 90th percentile and is recalculated periodically.
Column 15: The value represents the 97th percentile and is recalculated periodically.
Canadian Savers (product #17C0009)
Start of text box
Line 120 – Taxable amount of dividends from taxable Canadian corporations
Line 121 – Interest and other investment income
End of text box
This databank provides information on taxfilers who have been classified as savers.
Savers are defined as taxfilers who reported interest and investment income on line 121, but no dividend income on line 120 of the personal income tax return.
Interest and investment income sources would include interest from Canada Savings bonds, bank accounts, treasury bills, investment certificates, term deposits, earnings on life insurance policies as well as foreign interest and dividend income.
Dividend income would include dividends from taxable Canadian corporations (as stocks or mutual funds), but not dividends from foreign investments.
Taxfilers reporting Canadian dividend income would not be counted as savers, but would be classified as investors.
The content of the databank is as follows:
Table 1: Summary
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Number of savers
Column 8 – Average age of savers
Column 9 – Median total income of savers
Column 10 – Total amount of interest dollars reported (in thousands of dollars)
Column 11 – Median of interest dollars
Table 2: Age groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of savers
Column 8 – Percent of savers 0-24 years of age
Column 9 – Percent of savers 25-34 years of age
Column 10 – Percent of savers 35-44 years of age
Column 11 – Percent of savers 45-54 years of age
Column 12 – Percent of savers 55-64 years of age
Column 13 – Percent of savers 65+ years of age
Column 14 – Total amount of interest income dollars reported (in thousands of dollars)
Column 15 – Percent of interest income reported by age group 0-24
Column 16 – Percent of interest income reported by age group 25-34
Column 17 – Percent of interest income reported by age group 35-44
Column 18 – Percent of interest income reported by age group 45-54
Column 19 – Percent of interest income reported by age group 55-64
Column 20 – Percent of interest income reported by age group 65+
Table 3: Sex
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Percent of taxfilers who are male
Column 8 – Percent of taxfilers who are female
Column 9 – Total number of savers
Column 10 – Percent of savers who are male
Column 11 – Percent of savers who are female
Column 12 – Total amount of interest income reported (in thousands of dollars)
Column 13 – Percent of interest income reported by males
Column 14 – Percent of interest income reported by females
Column 15 – Median interest income of all savers
Column 16 – Median interest income of all male savers
Column 17 – Median interest income of all female savers
Table 4: Income groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of savers
Column 8 – Percent of savers with total income less than $20,000
Column 9 – Percent of savers with total income between $20,000 and $39,999
Column 10 – Percent of savers with total income between $40,000 and $59,999
Column 11 – Percent of savers with total income between $60,000 and $79,999
Column 12 – Percent of savers with total income $80,000+
Column 13 – Total amount of interest income reported (in thousands of dollars)
Column 14 – Percent of interest income reported by savers with total income less than $20,000
Column 15 – Percent of interest income reported by savers with total income between $20,000 and $39,999
Column 16 – Percent of interest income reported by savers with total income between $40,000 and $59,999
Column 17 – Percent of interest income reported by savers with total income between $60,000 and $79,999
Column 18 – Percent of interest income reported by savers with total income $80,000+
Canadian Investors (product #17C0007)
Start of text box
Line 120 – Taxable amount of dividends from taxable Canadian corporations
Line 121 – Interest and other investment income
End of text box
This databank provides information on taxfilers classified as investors.
Investors include taxfilers who reported dividend income on line 120 of their personal tax return. They may or may not have also reported interest and other investment income on line 121. When income is also reported on line 121, that amount is added to the amount of dividend income received, and the sum becomes the investment income of the investor.
The content of the databank is as follows:
Table 1: Summary
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Number of investors
Column 8 – Average age of investors
Column 9 – Median total income of investors
Column 10 – Amount of investment dollars (in thousands of dollars)
Column 11 – Percentage of the investment income derived from dividends
Column 12 – Median investment income
Table 2: Age groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of investors
Column 8 – Percent of investors 0-24 years of age
Column 9 – Percent of investors 25-34 years of age
Column 10 – Percent of investors 35-44 years of age
Column 11 – Percent of investors 45-54 years of age
Column 12 – Percent of investors 55-64 years of age
Column 13 – Percent of investors 65+ years of age
Column 14 – Total amount of investment income dollars reported (in thousands of dollars)
Column 15 – Percent of investment income reported by age group 0-24
Column 16 – Percent of investment income reported by age group 25-34
Column 17 – Percent of investment income reported by age group 35-44
Column 18 – Percent of investment income reported by age group 45-54
Column 19 – Percent of investment income reported by age group 55-64
Column 20 – Percent of investment income reported by age group 65+
Table 3: Sex
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Percent of taxfilers who are male
Column 8 – Percent of taxfilers who are female
Column 9 – Total number of investors
Column 10 – Percent of investors who are male
Column 11 – Percent of investors who are female
Column 12 – Total amount of investment income reported (in thousands of dollars)
Column 13 – Percent of investment income reported by males
Column 14 – Percent of investment income reported by females
Column 15 – Median investment income of all investors
Column 16 – Median investment income of all male investors
Column 17 – Median investment income of all female investors
Table 4: Income groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of investors
Column 8 – Percent of investors with total income less than $20,000
Column 9 – Percent of investors with total income between $20,000 and $39,999
Column 10 – Percent of investors with total income between $40,000 and $59,999
Column 11 – Percent of investors with total income between $60,000 and $79,999
Column 12 – Percent of investors with total income $80,000+
Column 13 – Total amount of investment income reported (in thousands of dollars)
Column 14 – Percent of investment income reported by investors with total income less than $20,000
Column 15 – Percent of investment income reported by investors with total income between $20,000 and $39,999
Column 16 – Percent of investment income reported by investors with total income between $40,000 and $59,999
Column 17 – Percent of investment income reported by investors with total income
between $60,000 and $79,999
Column 18 – Percent of investment income reported by investors with total income
$80,000+
Canadian Investment Income (product #17C0008)
Start of text box
Line 120 – Taxable amount of dividends from taxable Canadian corporations
Line 121 – Interest and other investment income
End of text box
This databank provides information on taxfilers who reported dividend income on line 120 of the tax return, or interest and other investment income on line 121, or both. These taxfilers include those designated as savers and those designated as investors in two other databanks available: Canadian Savers and Canadian Investors. In this databank, investment income includes both interest and dividends.
Dividend income includes dividends from taxable Canadian corporations (as stocks or mutual funds).
Interest and other investment income sources include interest from Canada Savings bonds, bank accounts, treasury bills, investment certificates, term deposits, earnings on life insurance policies as well as foreign interest and dividend income.
The content of the databank is as follows:
Table 1: Summary
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Number of taxfilers with investment income
Column 8 – Average age of taxfilers with investment income
Column 9 – Median total income of taxfilers with investment income
Column 10 – Reported investment income dollars for all taxfilers with investment income (in thousands of dollars)
Column 11 – Median investment income for all taxfilers with investment income
Table 2: Age groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of receivers of investment income
Column 8 – Percent of receivers of investment income 0-24 years of age
Column 9 – Percent of receivers of investment income 25-34 years of age
Column 10 – Percent of receivers of investment income 35-44 years of age
Column 11 – Percent of receivers of investment income 45-54 years of age
Column 12 – Percent of receivers of investment income 55-64 years of age
Column 13 – Percent of receivers of investment income 65+ years of age
Column 14 - Total amount of investment income dollars reported (in thousands of dollars)
Column 15 – Percent of investment income reported by age group 0-24
Column 16 – Percent of investment income reported by age group 25-34
Column 17 – Percent of investment income reported by age group 35-44
Column 18 – Percent of investment income reported by age group 45-54
Column 19 – Percent of investment income reported by age group 55-64
Column 20 – Percent of investment income reported by age group 65+
Table 3: Sex
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Percent of taxfilers who are male
Column 8 – Percent of taxfilers who are female
Column 9 – Total number of receivers of investment income
Column 10 – Percent of receivers of investment income who are male
Column 11 – Percent of receivers of investment income who are female
Column 12 – Total amount of investment income reported (in thousands of dollars)
Column 13 – Percent of investment income reported by males
Column 14 – Percent of investment income reported by females
Column 15 – Median investment income of all receivers of investment income
Column 16 – Median investment income of all male receivers of investment income
Column 17 – Median investment income of all female receivers of investment income
Table 4: Income groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Total number of receivers of investment income
Column 8 – Percent of receivers of investment income with total income less than $20,000
Column 9 – Percent of receivers of investment income with total income between $20,000 and $39,999
Column 10 – Percent of receivers of investment income with total income between $40,000 and $59,999
Column 11 – Percent of receivers of investment income with total income between $60,000 and $79,999
Column 12 – Percent of receivers of investment income with total income $80,000+
Column 13 – Total amount of investment income reported (in thousands of dollars)
Column 14 – Percent of investment income reported by receivers of investment income with total income less than $20,000
Column 15 – Percent of investment income reported by receivers of investment income with total income between $20,000 and $39,999
Column 16 – Percent of investment income reported by receivers of investment income with total income between $40,000 and $59,999
Column 17 – Percent of investment income reported by receivers of investment income with total income between $60,000 and $79,999
Column 18 – Percent of investment income reported by receivers of investment income with total income $80,000+
Canadian Capital Gains (product #17C0012)
Start of text box
Line 127 – Taxable amount of capital gains
End of text box
This databank provides information on taxfilers who reported capital gains during the tax year under review.
Line 127 of the T1 income tax return contains the amount of taxable capital gains reported by Canadians; this value is half the actual capital gains received. The information in this databank reflects the total capital gains received; amounts reported have been grossed up to reflect this total.
The content of the databank is as follows:
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Total number of taxfilers
Column 7 – Number of taxfilers reporting capital gains
Column 8 – Percent of taxfilers reporting capital gains who had a total income under $20,000
Column 9 – Percent of taxfilers reporting capital gains who had a total income between $20,000 and $39,999
Column 10 – Percent of taxfilers reporting capital gains who had a total income between $40,000 and $59,999
Column 11 – Percent of taxfilers reporting capital gains who had a total income between $60,000 and $79,999
Column 12 – Percent of taxfilers reporting capital gains who had a total income of $80,000+
Column 13 – Total value of capital gains (in thousands of dollars)
Column 14 – Percent of capital gains reported by taxfilers with a total income under $20,000
Column 15 – Percent of capital gains reported by taxfilers with a total income between $20,000 and $39,999
Column 16 – Percent of capital gains reported by taxfilers with a total income between $40,000 and $59,999
Column 17 – Percent of capital gains reported by taxfilers with a total income between $60,000 and $79,999
Column 18 – Percent of capital gains reported by taxfilers with a total income of $80,000+
Canadian Taxfilers (product #17C0010)
This databank provides a demographic and income profile of Canadians who filed a personal tax return in the reference year, according to the T1 preliminary file.
The content of the databank is as follows:
Table 1: Summary
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Number of taxfilers
Column 7 – Percent of taxfilers 0-24 years of age
Column 8 – Percent of taxfilers 25-34 years of age
Column 9 – Percent of taxfilers 35-44 years of age
Column 10 – Percent of taxfilers 45-54 years of age
Column 11 – Percent of taxfilers 55-64 years of age
Column 12 – Percent of taxfilers 65+ years of age
Column 13 – Average age of taxfilers
Column 14 – Median total income of taxfilers
Column 15 – 75th percentile of total income of taxfilers
Column 16 – 85th percentile of total income of taxfilers
Column 17 – 95th percentile of total income of taxfilers
Column 18 – Median employment income of taxfilers
Column 19 – 75th percentile of employment income of taxfilers
Table 2: Income Groups
Column 1 – City identification number
Column 2 – Postal area
Column 3 – Postal walk (no longer available)
Column 4 – Level of geography (see geography section)
Column 5 – Place name
Column 6 – Number of taxfilers
Column 7 – Percent of taxfilers with total income less than $20,000
Column 8 – Percent of taxfilers with total income between $20,000 and $39,999
Column 9 – Percent of taxfilers with total income between $40,000 and $59,999
Column 10 – Percent of taxfilers with total income between $60,000 and $79,999
Column 11 – Percent of taxfilers with total income $80,000+
Column 12 – Value of total income (in thousands of dollars)
Column 13 – Percent of total income reported by taxfilers with total income less than $20,000
Column 14 – Percent of total income reported by taxfilers with total income between $20,000 and $39,999
Column 15 – Percent of total income reported by taxfilers with total income between $40,000 and $59,999
Column 16 – Percent of total income reported by taxfilers with total income between $60,000 and $79,999
Column 17 – Percent of total income reported by taxfilers with total income $80,000+
Charitable Donations (product #13C0014)
Start of text box
Line 340 – Allowable charitable donations and government gifts
End of text box
This databank provides information on taxfilers classified as charitable donors. Charitable donors are defined as taxfilers reporting donations on line 340 of the tax return.
Canadians contribute in many ways to charitable organizations. The databank on charitable donors provides information on taxfilers who claimed a tax credit for charitable donations on their income tax return in the reference year. These data may include donations that might be denied by the Canada Revenue Agency (CRA) after an audit. To find out more about why donations might be denied (i.e. tax shelter gifting arrangements, false receipting) please go to the Canada Revenue Agency website.
Persons making charitable donations, but not reporting them on their personal tax return are not included in this databank. These include donations for which no receipt was provided and donations for which the receipt was lost. No estimate of such donations is included in these data.
Only donations made to approved organizations are allowable as deductions in the tax system. Donations are eligible if made to Canadian registered charities and Canadian amateur athletic associations. They are also eligible if made to: prescribed universities outside Canada; certain tax exempt housing organizations in Canada; Canadian municipalities; the United Nations; and certain charities outside Canada to which the Government of Canada has made a gift.
It is possible to carry donations forward for up to five years after the year in which they were made. In the reference year, it is possible to claim donations made in any of the previous five years, as long as they were not already claimed in a prior year. The donations made in the reference year could be claimed the same year, or could be carried forward to any of the next five years. According to tax laws, taxfilers are permitted to claim both their donations and those made by their spouses to get better tax benefits. Consequently, the number of persons who made charitable donations may be higher than the number who claimed tax credits.
A change in tax regulations was introduced in 2007. Taxfilers contributing to a recognized charity (as outlined above) were eligible to claim a tax credit of 15% of their donations on the first $200, and 29% on the rest. In 2006, the tax credit was 15.25% on the first $200 and 29% on the rest. In 2005, the tax credit was 15% on the first $200 and 29% on the rest. From 2001 to 2004, the tax credit was 16% on the first $200 and 29% on the rest. From 1992 to 2000, the tax credit was 17% on the first $200 and 29% on the rest. Previously, taxfilers had to give $250 to charity before the 29% credit was available.
The content of the databank is as follows:
Table 1: Summary
Column 1 - City identification number
Column 2 - Postal area
Column 3 - Postal walk (no longer available)
Column 4 - Level of geography (see Geography section)
Column 5 - Place name
Column 6 - Total Number of taxfilers
Column 7 - Number of charitable donors
Column 8 - Average age of donors
Column 9 - Average donation for age group 0-24
Column 10 - Average donation for age group 25-34
Column 11 - Average donation for age group 35-44
Column 12 - Average donation for age group 45-54
Column 13 - Average donation for age group 55-64
Column 14 - Average donation for age group 65+
Column 15 - Total amount of charitable donations (thousands of $)
Column 16 - Median donation
Column 17 - Median total income of donors
Column 18 - 75th percentile of donors' total income
Table 2: Age and Sex (new beginning with 1995)
Column 1 - City identification number
Column 2 - Postal area
Column 3 - Postal walk (no longer available)
Column 4 - Level of geography (see Geography section)
Column 5 - Place name
Column 6 - Total Number of taxfilers
Column 7 - Percent of taxfilers who are male
Column 8 - Percent of taxfilers who are female
Column 9 - Number of charitable donors
Column 10 - Percent of charitable donors who are male
Column 11 - Percent of charitable donors who are female
Column 12 - Percent of donors 0 - 24 years of age
Column 13 - Percent of donors 25 - 34 years of age
Column 14 - Percent of donors 35 - 44 years of age
Column 15 - Percent of donors 45 - 54 years of age
Column 16 - Percent of donors 55 - 64 years of age
Column 17 - Percent of donors 65+ years of age
Column 18 - Total median donation
Column 19 - Median donation of males
Column 20 - Median donation of females
Column 21 - Total amount of charitable donations (thousands of $)
Column 22 - Total amount of charitable donations for males (thousands of $)
Column 23 - Total amount of charitable donations for females (thousands of $)
Table 3: Income Groups (new beginning with 1997)
Column 1 - City identification number
Column 2 - Postal area
Column 3 - Postal walk (no longer available)
Column 4 - Level of geography (see Geography section)
Column 5 - Place name
Column 6 - Total number of taxfilers
Column 7 - Total number of charitable donors
Column 8 - Percent of charitable donors with total income less than $20,000
Column 9 - Percent of charitable donors with total income between $20,000 and $39,999
Column 10 - Percent of charitable donors with total income between $40,000 and $59,999
Column 11 - Percent of charitable donors with total income between $60,000 and $79,999
Column 12 - Percent of charitable donors with total income $80,000+
Column 13 - Total value of charitable donations (in thousands of dollars)
Column 14 - Percent of donations reported by donors with total income under $20,000
Column 15 - Percent of donations reported by donors with total income between $20,000 and $39,999
Column 16 - Percent of donations reported by donors with total income between $40,000 and $59,999
Column 17 - Percent of donations reported by donors with total income between $60,000 and $79,999
Column 18 - Percent of donations reported by donors with total income $80,000+
Statistical Tables - Footnotes and Historical Availability
RRSP Contributors
- Table 1 is available in its current format starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1994 data and federal electoral districts (FEDs) with the 1997 data.
- Table 2 (age groups) and table 3 (sex) are available in their current formats starting with the 1994 data, for postal areas, CMAs, CDs and FEDs (since 1997). Some changes were made to the age groupings over the years.
- Table 4 (income groups) is available in its current format starting with the 2007 data, for postal areas, CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
RRSP Contribution Limits (Room)
- Both tables are available in their current format starting with the 1993 data.
- Data are available for all levels of the postal geography starting with the 1993 tax year.
- Data for census metropolitan areas (CMAs) are available starting with the 1993 tax year (1994 room), census divisions (CDs) with the 1994 tax year (1995 room) and federal electoral districts (FEDs) with the 1997 tax year (1998 room).
- The figures in Table 2 ($500, $2,400, $4,700, $7,800 and $13,000) represent the 25th, 50th, 75th, 90th and 97th percentiles of new room and are recalculated periodically.
Canadian Savers
- Table 1 is available in its current format starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1995 data and federal electoral districts (FEDs) with the 1997 data.
- Table 2 (age groups) and table 3 (sex) are available in their current formats starting with the 1995 data, for postal areas, CMAs, CDs and FEDs (since 1997). Some changes were made to the age groupings over the years.
- Table 4 (income groups) is available in its current format starting with the 2007 data, for postal areas, CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
Canadian Investors
- Table 1 is available in its current format starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1995 data and federal electoral districts (FEDs) with the 1997 data.
- The proportion of investment income from dividends is available starting with the 1996 data (Table 1).
- Table 2 (age groups) and table 3 (sex) are available in their current formats starting with the 1995 data, for postal areas, CMAs, CDs and FEDs (since 1997). Some changes were made to the age groupings over the years.
- Table 4 (income groups) is available in its current format starting with the 2007 data, for postal areas, CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
Canadian Investment Income
- Table 1 is available in its current format starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1995 data and federal electoral districts (FEDs) with the 1997 data.
- Table 2 (age groups) and table 3 (sex) are available in their current formats starting with the 1995 data, for postal areas, CMAs, CDs and FEDs (since 1997). Some changes were made to the age groupings over the years.
- Table 4 (income groups) is available in its current format starting with the 2007 data, for postal areas, CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
Canadian Capital Gains
- The standard table on capital gains by income group is available in its current format starting with the 2007 data. From 1998 data up to 2006, the income groups were cumulative.
- All levels of geography are available since the 1998 data, including census divisions, census metropolitan areas, federal electoral districts and all levels of the postal geography.
Canadian Taxfilers
- Table 1 is available in its current format starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1995 data and federal electoral districts (FEDs) with the 1997 data.
- Starting with the 2007 data, the column on the "% reporting in French" in table 1 has been suppressed.
- Table 2 (income groups) is available in its current format starting with the 2007 data, for postal areas, CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
Charitable Donations
- Table 1 (summary) is available starting with the 1990 data, according to the postal geography. Census metropolitan areas (CMAs) are available starting with the 1993 data, census divisions (CDs) with the 1995 data and federal electoral districts (FEDs) with the 1997 data.
- Changes were made to the age groups in table 1 in 1991 and in 1997.
- Table 2 (age groups) is available starting with the 1995 data, for the postal geography and for CMAs. CDs are available starting with the 1995 data and FEDs with the 1997 data.
- Changes were made to the age groups in table 2 in 1997.
- Table 3 (Income groups) is available in its current format starting with the 2007 data, for the postal geography, for CMAs, CDs and FEDs. From 1997 to 2006, the income groups were cumulative.
Glossary of Terms
75th percentile
Total income values are ranked from highest to lowest and the value reported as being the 75th percentile indicates that 25% of the taxfilers report an income equal or above that amount and 75% fall below. Percentiles are calculated for each geographical level.
For example, if the 75th percentile of total income is shown as $60,000 this means that 25% of the population under review has a total income greater than or equal to $60,000 and 75% of the population has a total income less than or equal to $60,000.
85th percentile
Starting with the 2007 data, the dollar value of the 85th percentile appears in the tables instead of the percentage above the 85th percentile like it was in previous years. Total income values are ranked from highest to lowest and the value reported as being the 85th percentile indicates that 15% of the taxfilers report an income equal or above that amount and 85% fall below. Percentiles are calculated for each geographical level.
For example, if the 85th percentile of total income is shown as $65,000 this means that 15% of the taxfilers has a total income greater than or equal to $65,000
95th percentile
Starting with the 2007 data, the dollar value of the 95th percentile appears in the tables instead of the percentage above the 95th percentile like it was in previous years. Total income values are ranked from highest to lowest and the value reported as being the 95th percentile indicates that 5% of the taxfilers report an income equal or above that amount and 95% fall below. Percentiles are calculated for each geographical level.
For example, if the 95th percentile of total income is shown as $90,000 this means that 5% of the population under review has a total income greater than or equal to $90,000
Age
Calculated as of December 31 of the reference year (i.e., tax year minus year of birth). Starting in 2007, all the counts are rounded to the nearest 10.
Capital Gains
Line 127 of the T1 income tax return shows "taxable capital gains" or half of the capital gains actually received. The information in this databank has been grossed up to represent the total capital gains received.
Charitable donation
Is the allowable portion of total donations, as reported on the income tax return. Canadians contribute in many ways to charitable organizations. These data include only amounts given to charities and approved organizations for which official tax receipts were provided and claimed on tax returns. It is possible to carry donations forward for up to five years after the year in which they were made. Therefore, donations reported for the 2012 taxation year could include donations that were made in any of the five previous years. According to tax laws, taxfilers are permitted to claim both their donations and those made by their spouses to receive better tax benefits. Consequently, the number of people who made charitable donations may be higher than the number who claimed tax credits.
Charitable donor
Is defined as a taxfiler reporting a charitable donation amount on line 340 of the personal income tax form.
CityID
Since municipality names can be, in some cases, quite long and cumbersome for handling in electronic files, municipalities are given a "city identification number". Starting in 2007, the CityID is a five digits alpha-numeric component. It is created with the first letter of Postal CodeOM followed by "9" and a four digits number. Each first letter of Postal Code is allocated a range of number from 1 to 9999 (more explanation in geography section).
Deferred profit sharing plan (DPSP)
An employer-sponsored savings plan registered by the Canada Revenue Agency. Contributions to these plans by the employer (employees cannot contribute) are based on profits. The amount accumulated in these plans can be paid out as a lump sum at retirement or termination of employment, transferred to an RRSP, received in instalments over a period not to exceed ten years, or used to purchase an annuity.
Dividend income
Includes taxable amount of dividends (eligible and other than eligible) received from taxable Canadian corporations (as stocks or mutual funds) as reported on line 120 of the personal income tax return, and then grossed down to the actual amounts received; dividend income does not include dividends received from foreign investments (which are included in interest income and reported on line 121).
Earned income
The income used to determine the RRSP deduction limit. It includes such items as employment income (less union dues and expenses), net business and rental income, disability payments and alimony received. Alimony payments, current year business and rental losses are deducted from this amount. Most investment income (other than rents) is not considered earned income. In calculating the RRSP deduction limit, earned income from the previous year is used.
Employment income
The total reported employment income. Employment income includes wages and salaries, commissions from employment, training allowances, tips and gratuities, and self-employment income (net income from business, profession, farming, fishing and commissions) and Tax Exempted Indian Employment Income (new in 1999 for wages and salaries, commissions, and in 2010 for self-employment income).
Interest income
Refers to the amount Canadians claimed on line 121 of the personal income tax return. This amount includes interest generated from bank deposits, Canada Savings Bonds, corporate bonds, treasury bills, investment certificates, term deposits, annuities, mutual funds, earnings on life insurance policies and all foreign interest and foreign dividend incomes.
Investment income
Includes both interest income and dividend income.
Investors
Taxfilers who reported dividend income on line 120 of their personal tax return. They may or may not have also reported interest and other investment income on line 121. When such income is reported on line 121, this amount is added to the amount of dividend income received, and the sum becomes the investment income of the investor.
Level of geography
Is a code designating the type of geographic area to which the information in the table applies. See the section on Geography for further information.
Median
The middle number in a group of numbers. Where a median income, for example, is given as $26,000, it means that exactly half of the incomes reported are greater than or equal to $26,000, and that the other half is less than or equal to the median amount. Zero values are not included in the calculation of medians for individuals.
New room
For 2013 this amount is calculated as 18% of 2012 earned income (from definition above) to a maximum of $23,820 minus pension adjustment (PA) minus past service pension adjustment (PSPA). Since the focus of these data is for net new room for potential RRSP contributions, PA and/or PSPA details will be omitted.
Past service pension adjustment (PSPA)
Applies only to members of defined benefit RPPs. A PSPA occurs when the pension benefit is upgraded, or additional credits purchased, for service in past years. In the first case, it is called an exempt (from certification) PSPA; in the second case, a certifiable PSPA. Only service after 1989 is considered.
Pension adjustment (PA)
Calculated value of the pension accrued in the year in an RPP or a DPSP. The PA decreases the RRSP deduction limit. To calculate this limit, the PA from the previous year is used.
Registered disability savings plan income (RDSP)
Beginning in 2008, the RDSP is for individuals for whom a valid disability certificate has been filed. Contributions can be made by the beneficiary or by qualified persons legally authorized to act for the beneficiary. The contributions are not deductible but the income earned is not taxable as long as it remains into the plan. Contributions are subject to a lifetime limit of $200,000; they will be matched in some degree by government contributions.
Registered pension plan (RPP)
An employer-sponsored plan registered with the Canada Revenue Agency and most commonly also with one of the pension regulatory authorities. The purpose of such plans is to provide employees with a regular income at retirement. The two main types of RPPs are called defined benefit (where the benefit formula is specified) and defined contribution (where only the contribution formula is defined).
Registered retirement savings plan (RRSP)
An individual retirement savings plan that is registered by the Canada Revenue Agency. It permits limited contributions, and income earned in the RRSP is exempt from tax until payments are received from the plan.
Savers
Taxfilers who reported interest and investment income on line 121 of the personal income tax return, but no dividend income on line 120.
Taxfiler
Individual who filed a personal income tax return for the reference year.
Total income
Note: this variable was revised over the years, as reflected in the comments below; data users who plan to compare current data to data from previous years should bear in mind these changes. Also, it should be noted that all income amounts are gross, with the exception of net rental income, net limited partnership income and all forms of net self-employment income.
Income reported by tax filers from any of the following sources:
- Employment income
- Wages/Salaries/Commissions;
- Other Employment Income as reported on line 104 of the tax form (tips, gratuities, royalties, etc.);
- Net Self-Employment;
- Tax Exempted Employment Income for Indians (Wages/Salaries/Commissions) for Indians (new in 1999);
- Tax Exempted Self-Employment Income for Indians (since 2010).
- Investments
- Interest and other investment income;
- Dividend income.
- Government Transfers
- Employment Insurance
- Unemployment Insurance/Employment Insurance since 1982;
- Quebec Parental Insurance Plan since 2006.
- Pension Income
- Old Age Security since 1982;
- Net Federal Supplements (previously included in other income, shown separately since 1992)
- Guaranteed Income Supplement created in 1967 and Spousal Allowance created in 1975, available since 1992;
- Spousal Allowance (included in Net Federal Supplements since 1992; previously included in non-taxable income;
- Canada and Quebec Pension plans benefits, since 1982.
- Child Benefit
- Family Allowance program up to 1992
- Child Tax Credit up to 1992
- Canada Child Tax Benefit (starting with 1993)
- Universal Child Care Benefit since 2006
- Federal Tax, Goods and Services Tax, Harmonized Sales Tax
- Federal Sales Tax Credit (from 1988 to 1990);
- Goods and Services Tax (GST) credit from 1990 to 1996;
- Harmonized Sales Tax (HST) credit since 1997.
- Workers' Compensation (included in other income prior to 1992 and shown separately since 1992)
- Social Assistance (included in other income prior to 1992 and shown separately since 1992)
- Provincial Refundable Tax Credits/Family Benefits – for a complete list please see the "Provincial Refundable Tax Credits/Family Benefits" section
- Other Government Transfers
- Working Income Tax Benefit (starting in 2007 depending on the province or territory; included since 2010 in the statistical tables).
- Employment Insurance
- Private Pensions
- Registered Retirement Savings Plan Income (since 1994; previously in "other income"; since 1999, only for tax filers 65+)
- Other Income
- Included as 'other income' prior to 1990
- Net limited partnership income;
- Alimony;
- Net rental income;
- Income for non-filing spouses (since 1989; included in "other income");
- Other incomes as reported on line 130 of the tax form (fellowships, bursaries, etc.);
- Registered Disability Savings Plan (RDSP) Income as reported on line 125 of the tax form (introduced in 2008).
- Included as 'other income' prior to 1990
Monies not included in income above are: veterans' disability and dependent pensioners' payments, war veterans' allowances, lottery winnings and capital gains.
Total room (in thousands of dollars)
The sum of "new room" and "unused room" as defined here.
Total room (number of persons)
The number of taxfilers who have either unused room from previous years, new room based on their earned income, or both. The number of persons with total room does not correspond to the sum of persons with new room and unused room, as an individual can be included in both categories.
Universal Child Care Benefit
Beginning in July 2006, the Universal Child Care Benefit (UCCB) is a taxable amount of $100 paid monthly for each child under 6 years of age. Included in Canada Child Tax Benefits in the statistical tables.
Unused RRSP contribution room (unused room)
The amount of the RRSP deduction limit that is not claimed by the taxfiler, or the amount remaining after subtracting actual contributions claimed on the tax return from that year's contribution room. Unused room can be carried forward indefinitely. The first year of unused room is from 1991 (see table B).
Geography
The data are available for the following geographic areas. See "Statistical Tables - Footnotes and Historical Availability" for further details. The mailing address at the time of filing is the basis for the geographic information in the tables.
Standard areas
Canada
Provinces and territories
Postal Geography:
- City Totals
- Urban Forward Sortation Areas (excludes Rural Routes and Suburban Services, and Other Urban Areas within City)
- Suburban Services*
- Rural Routes (Within City)*
- Rural Postal Code Areas (Within City)
- Other Urban Areas (Non-residential within city)
- Rural Communities (not in City)
- Other Provincial Totals
*These postal geography levels were available in the past but are no longer available for this data.
Some postal geography levels such as Postal Walks are no longer available for this data.
Census Geography
- Economic Regions
- Census Divisions
- Census Metropolitan Areas
- Census Agglomerations
- Census Tracts
- Federal Electoral Districts (2003 Representation Order)
User-defined areas:
Users may select a specific area of interest that is not a standard area for which data can be made available in standard format. To obtain data, provide us with a list of the Postal Codes for which data are required and we will provide the aggregated data. Of course, the area must satisfy our confidentiality requirements, or no data can be produced. See the "Special Geography" section for further information.
Geographic Levels – Postal Geography
The various data compiled from the taxfile are available for different levels of the postal geography. Coded geographic indicators appearing on the data tables are shown below with a brief description.
| Level of Geography (L.O.G.) |
Postal Area | Description |
|---|---|---|
| 12 | Canada | This level of data is an aggregation of the provincial/territorial totals (code 11). The national total is identified by the region code Z99099. |
| 11 | Province or Territory Total | This level of data is an aggregation of the following geographies within a province: City Totals = Code 08 Rural Communities = Code 09 Other Provincial Totals = Code 10 These totals are identified by a provincial/territorial postal letter, then a "990" followed by the province/territory code, as follows: Newfoundland and Labrador = A99010 Nova Scotia = B99012 Prince Edward Island = C99011 New Brunswick = E99013 Quebec = J99024 Ontario = P99035 Manitoba = R99046 Saskatchewan = S99047 Alberta = T99048 British Columbia = V99059 Northwest Territories = X99061 Nunavut = X99062 Yukon Territory = Y99060 |
| 10 | Other Provincial Total ("P" Pot) |
This level of data is an aggregation of small communities in the province that had less than 100 taxfilers, where these communities are combined into a "pot". Before 1992, it was identified by the same codes as the provincial/territorial totals, and only the "Delivery Mode" codes 2 and 3 distinguished between the two. To avoid this problem, starting with the 1992 data, an "8" appears after the provincial/territorial letter instead of a "9". The "9" will be reserved for the provincial/territorial total, as explained in 11 above. These "pot" codes are as follows: Newfoundland and Labrador = A89010 Nova Scotia = B89012 Prince Edward Island = C89011 New Brunswick = E89013 Quebec = J89024 Ontario = P89035 Manitoba = R89046 Saskatchewan = S89047 Alberta = T89048 British Columbia = V89059 Northwest Territories = X89061 Nunavut = X89062 Yukon Territory = Y89060 |
| 09 | Rural Communities (Not in City ) | For data obtained prior to reference year 2011, this level of geography was called “Rural Postal Codes (Not in a City)”. This level of geography pertains to rural communities that have one and only one rural Postal Code. Rural Postal Codes can be identified by a "zero" in the second position of the Postal Code. The 2013 databanks contain 3,962 areas coded as level of geography 09. |
| 08 | City Total | This level of data is an aggregation of the following geographies for unique place names within a province/territory: Urban FSA (Residential) = Code 03 Rural Route= Code 04 Suburban Services = Code 05 Rural Postal Code Areas (within city) = Code 06 Other Urban Area = Code 07 As of 2011, data for L.O.G. 04 and 05 are suppressed but included in the city totals. They have the following format: e.g., Edmonton = T95479; Regina = S94876. The pattern is the postal letter of the city plus "9" in the second position (indicating a total), followed by a 4 digit numeric code for the community (often called "CityID"). In general, postal cities do not coincide exactly with census subdivisions. The 2013 databanks contain 1,657 areas coded as level of geography 08. |
| 07 | Other Urban Area (Non-residential within city - "E" Pot) |
This aggregation of data (or "pot") covers non-residential addresses within an urban centre and all other data not otherwise displayed. Commercial addresses, post office boxes and general delivery are included, as are residential addresses with too few taxfilers to report separately. They can be recognized by codes that are similar to the city totals, with a distinguishing difference: an "8" will follow the city postal letter rather than the "9" of the city total (e.g., Edmonton = T85479; Regina = S84876). The 2013 databanks contain 443 areas coded as level of geography 07. |
| 06 | Rural Postal Code Areas (Within City) | For data obtained prior to reference year 2011, this level of geography was called “Rural Postal Codes (Within a City)”. These data pertain to rural Postal Codes that belong to communities with more than one rural Postal Code. These occur in areas that were formerly serviced by rural delivery service and changed by Canada Post to urban delivery service or in communities served by more than one rural Postal Code. Rural Postal Codes can be identified by a "zero" in the second position of the Postal Code. Although data is disseminated individually for each rural Postal Code associated with a community, only the community name appears with the disseminated data. The actual rural Postal Codes are not displayed with the disseminated data. Therefore, for this level of geography, community names will appear more than once. The 2013 databanks contain 583 areas coded as level of geography 06. |
| 05 | Suburban Service | No longer available. Sparsely populated fringe areas of urban centres may receive their postal service from an urban post office by delivery designated as "suburban service". Their region code retains all six characters of the Postal Code. Suburban Services are usually near or on the perimeters of urban areas, and mail is delivered by a contractor to group mail boxes, community mail boxes and/or external delivery sites (e.g., kiosks, miniparks). |
| 04 | Rural Route | No longer available. Reasonably well-settled rural areas may receive their postal service from an urban post office by delivery designated as "rural route". Mail is delivered by a contractor to customers living along or near well-defined roads. Their region code retains all six characters of the Postal Code. |
| 03 | Urban FSA (Residential Area) |
The urban Forward Sortation Area (FSA, identified by the first three characters of the Postal Code) includes all residential addresses covered by the first three characters of a Postal Code in a particular urban area (not including levels 04 and 05). Only residential FSAs are considered for these databanks. An Urban FSA of this type can be identified by the FSA followed by three blanks. One FSA can be split in different parts if it is associated with more than one city. The 2013 databanks contain 2,450 areas coded as level of geography 03. |
Adding Postal Areas Without Duplication
Data files according to the postal geography will often contain subtotals and totals. Many data users need to add certain geographies in order to come up with a total for their particular area of interest. However, including subtotals during this process results in double-counting some populations, and this leads to an erroneous total. The following is a summary of which postal areas are aggregations in the standard postal geography.
Urban FSAs (LOG 3), Rural Routes (LOG 4), suburban services (LOG 5), Rural Postal Code Areas within a city (LOG 6) and Other Urban Areas (LOG 7) add up to City Totals (LOG 8).
City Totals (LOG 8), Rural Communities not in a city (LOG 9) and Other Provincial Totals (LOG 10) add up to provincial/territorial totals (LOG 11).
Provincial/territorial totals (LOG 11) add up to the Canada total (LOG 12).
Thus, using the Level of geography codes:
3 + 4 + 5 + 6 + 7 = 8
8 + 9 + 10 = 11
City identification number (CityID)
As of 2007, CityID has been modified.
Previous to 2007:
- CityID was a 4 digits number
- Each municipality had a unique number between 1 and 9999
- Almost every number was allocated to a municipality. Few numbers remained available for future new municipalities.
Starting with 2007 data:
To create more possibilities without changing the CityID length in our systems:
- CityID number is now combined with 1st letter of Postal Code
- Each 1st letter of Postal Code has a possibility of numbers, ranged from 1 to 9999 (Table D)
- Old numbers have been kept for existing municipality and 1st letters of Postal Code have been added to them (Table C)
- New municipalities have been assigned a new CityID number in new format (Table C)
| Postal Code | Municipality name | 2006 and Prior | 2007 and Follow |
|---|---|---|---|
| K1A xxx | Ottawa | 2434 | K2434 |
| G3C xxx | Stoneham-et-Tewkesbury | n/a | G2 |
| Province | Letter file | Range of number |
|---|---|---|
| Newfoundland & Labrador | A | 1 – 9999 |
| Prince Edward Island | C | 1 – 9999 |
| Nova Scotia | B | 1 – 9999 |
| New Brunswick | E | 1 – 9999 |
| Quebec | G | 1 – 9999 |
| Quebec | H | 1 – 9999 |
| Quebec | J | 1 – 9999 |
| Ontario | K | 1 – 9999 |
| Ontario | L | 1 – 9999 |
| Ontario | M | 1 – 9999 |
| Ontario | N | 1 – 9999 |
| Ontario | P | 1 – 9999 |
| Manitoba | R | 1 – 9999 |
| Saskatchewan | S | 1 – 9999 |
| Alberta | T | 1 – 9999 |
| British Columbia | V | 1 – 9999 |
| Yukon | Y | 1 – 9999 |
| Northwest Territories | X | 1 – 9999 |
| Nunavut | X | 1 – 9999 |
Therefore, it is now essential to identify a municipality by adding the Postal Code 1st letter to the number in order to get the proper municipality in the proper province (Table E):
| Letter | Number | Municipality name | Province |
|---|---|---|---|
| A | 2 | Avondale | NL |
| B | 2 | Bible Hill | NS |
| T | 2 | Rocky View | AB |
| G | 2 | Stoneham-et-Tewkesbury | QC |
Hierarchy of postal geography
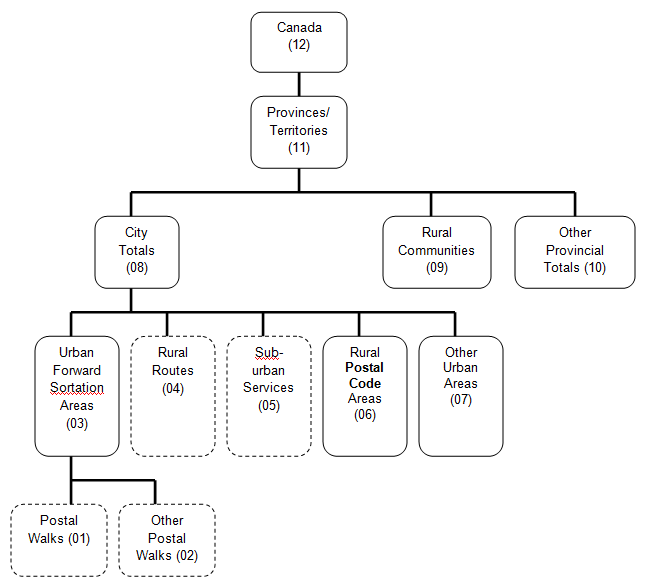
Description for Hierarchy of postal geography
Geographic Levels – Census Geography
Data are also available for the following levels of the Census geography; the following table shows the coded designators for these geographies, as well as a brief description of each.
| Level of Geography (L.O.G.) |
Area | Description |
|---|---|---|
| 12 | Canada | This level of data is an aggregation of the provincial/territorial totals (L.O.G. 11). The national total is identified by the region code Z99099. |
| 11 | Province or Territory Total | These totals are identified by a provincial/territorial postal letter, then a "990" followed by the province/territory code, as follows: Newfoundland and Labrador = A99010 Nova Scotia = B99012 Prince Edward Island = C99011 New Brunswick = E99013 Quebec = J99024 Ontario = P99035 Manitoba = R99046 Saskatchewan = S99047 Alberta = T99048 British Columbia = V99059 Northwest Territories = X99061 Nunavut = X99062 Yukon Territory = Y99060 |
| 61 | Census Tract | Census tracts (CTs) are small geographic units representing urban or rural neighbourhood-like communities in census metropolitan areas (see definition below) or census agglomerations with an urban core population of 50,000 or more at time of 1996 Census. CTs were initially delineated by a committee of local specialists (such as planners, health and social workers and educators) in conjunction with Statistics Canada. The 2013 databanks contain 5,365 areas coded as level of geography 61, based on 2011 Census. |
| 51 | Economic Region | An economic region is a grouping of complete census divisions (see definition below) with one exception in Ontario. Economic regions (ERs) are used to analyse regional economic activity. Within the province of Quebec, ERs are designated by law. In all other provinces, they are created by agreement between Statistics Canada and the provinces concerned. Prince Edward Island and the territories each consist of one economic region. The 2013 databanks contain 76 areas coded as level of geography 51, based on 2011 Census. |
| 42 | Census Agglomeration | The general concept of a census agglomeration (CA) is one of a very large urban area, together with adjacent urban and rural areas that have a high degree of economic and social integration with that urban area. CAs have an urban core population of at least 10,000, based on the previous census. The 2013 databanks contain 133 area codes as level of geography 42, based on the 2011 Census: 114 CAs, 6 provincial parts for the 3 CAs which cross provincial boundaries, and 13 residual geographies called Non CMA-CA, one for each province and territory. |
| 41 | Census Metropolitan Area | The general concept of a census metropolitan area (CMA) is one of a very large urban area, together with adjacent urban and rural areas that have a high degree of economic and social integration with that urban area. CMAs have an urban core population of at least 100,000, based on the previous census. The 2013 databanks contain 35 areas coded as level of geography 41, based on 2011 Census: 001, St. John's, Newfoundland and Labrador 205, Halifax, Nova Scotia 305, Moncton, New Brunswick 310, Saint John, New Brunswick 408, Saguenay, Quebec 421, Québec, Quebec 433, Sherbrooke, Quebec 442, Trois-Rivières, Quebec 462, Montréal, Quebec 505, Ottawa-Gatineau (3 items: combined, Quebec part and Ontario part) 521, Kingston, Ontario 529, Peterborough, Ontario 532, Oshawa, Ontario 535, Toronto, Ontario 537, Hamilton, Ontario 539, St-Catharines-Niagara, Ontario 541, Kitchener-Cambridge-Waterloo, Ontario 543, Brantford, Ontario 550, Guelph, Ontario 555, London, Ontario 559, Windsor, Ontario 568, Barrie, Ontario 580, Greater Sudbury, Ontario 595, Thunder Bay, Ontario 602, Winnipeg, Manitoba 705, Regina, Saskatchewan 725, Saskatoon, Saskatchewan 825, Calgary, Alberta 835, Edmonton, Alberta 915, Kelowna, British Columbia 932, Abbotsford-Mission, British Columbia 933, Vancouver, British Columbia 935, Victoria, British Columbia |
| 31 | Federal Electoral District | A federal electoral district (FED) refers to any place or territorial area represented by a member of Parliament elected to the House of Commons. There are 308 FEDs in Canada according to the 2003 Representation Order. The Representation Order is prepared by the Chief Electoral Officer describing, naming and specifying the population of each electoral district established by the Electoral Boundaries Commission and sent to the Governor in Council. The 2013 databanks contain 308 areas coded as level of geography 31. |
| 21 | Census Division | A census division (CD) is a group of neighbouring municipalities joined together for the purposes of regional planning and managing common services (such as police or ambulance services). A CD might correspond to a county, a regional municipality or a regional district. CDs are established under laws in effect in certain provinces and territories of Canada. In other provinces and territories where laws do not provide for such areas (Newfoundland and Labrador, Manitoba, Saskatchewan and Alberta), Statistics Canada defines equivalent areas for statistical reporting purposes in cooperation with these provinces and territories. The 2011 Census contain 293 areas coded as level of geography 21; however, the 2013 databanks contain 295 areas since the CD of Halton (Ont.) straddles 2 Economic Regions. Starting in 2007, Census divisions are identified in the tables by a six digits code: 2 first digits = Province 2 next digits = Economic Region 2 last digits = Census Division |
Geographic Levels – Special Geography
Clients may select geographical areas of their own definition; areas that are not part of the standard areas listed here (for example, bank service areas, retail store catchment areas). For this, clients must submit a list of the Postal Codes that make up their special area, and we will aggregate the micro data to correspond to that area of interest. Information ordered for special, or "user-defined" areas will be coded according to the following:
| Level of Geography (L.O.G.) |
Name | Description |
|---|---|---|
| 93 | Total for all user-defined areas | This level represents the sum total of all user-defined areas, and is the total of levels 91 and 92 described below. |
| 92 | Other user-defined areas | This level of geography represents all user-defined areas that were too small, in terms of population; to have information compiled on those areas individually (i.e. fewer than 100 taxfilers). Such areas are grouped into this "other" category. |
| 91 | Special user-defined area | Any area showing L.O.G. = 91 is an area defined by a specific user according to that user's needs (for example, school catchment areas, health districts, etc.) |
Conversion files
When a client is interested in purchasing data for areas that are considered non-standard geography by Income Statistics Division, a conversion file is usually necessary. A combination of Postal Codes making up one or more special area(s) is commonly referred to as a conversion file – an electronic file used by our staff to aggregate the different Postal Codes that make up the user-defined area. Simply provide us with the Postal Codes related to the area and we will compile the data (subject to our confidentiality restrictions).
For example, Postal Codes. User-defined areas may be branch service or school catchment areas, neighbourhoods or almost any other region.
We Invite Your Comments
We are always working on ways to improve our products. The comments we receive concerning quality and presentation are essential to meet this objective. If you have any suggestions in this regard, we encourage you, the user, to provide us with your comments.
How to obtain more information
Inquiries about these data and related statistics or services should be directed to:
Client Services, Income Statistics Division
Telephone: Toll Free 1-888-297-7355 or 613-951-7355
Statistics Canada, Jean Talon Building, 5th Floor
Ottawa, Ontario K1A 0T6
Online requests: income@statcan.gc.ca
Statistics Canada's National Contact Centre provides a wide range of services: identification of your needs, establishing sources or availability of data, consolidation and integration of data coming from different sources, and general support for the use of Statistics Canada concepts and the use of statistical data.
Statistics Canada's National Contact Centre
Telephone: Toll Free 1-800-263-1136 or 613-951-8116
Telecommunications device for the hearing impaired (TTY): 1-800-363-7629
Online requests: infostats@statcan.gc.ca
You can also visit us on the web: Statistics Canada.
Standards of service to the public
Statistics Canada is committed to serving its clients in a prompt, reliable and courteous manner and in the official language of their choice. To this end, the agency has developed standards of service which its employees observe in serving its clients. To obtain a copy of these service standards, please contact your nearest Statistics Canada Regional Reference Centre.
Copyright
Published by authority of the Minister responsible for Statistics Canada.
© Minister of Industry, 2014
All rights reserved. Use of this publication is governed by the Statistics Canada Open Licence Agreement.
© This data includes information copied with permission from Canada Post Corporation
List of available data products
The Income Statistics Division of Statistics Canada tabulates statistical data derived from administrative records - most notably, the taxfile. The resulting demographic and socio-economic databanks available are listed in the table below, along with their identifying product number and the usual release dates.
| Product name | Product number | Release date |
|---|---|---|
| RRSP Contributors | 17C0006 | Winter |
| RRSP Contribution Limits (Room) | 17C0011 | Winter |
| Canadian Savers | 17C0009 | Winter |
| Canadian Investors | 17C0007 | Winter |
| Canadian Investment Income | 17C0008 | Winter |
| Canadian Taxfilers | 17C0010 | Winter |
| Canadian Capital Gains | 17C0012 | Winter |
| Charitable Donors | 13C0014 | Winter |
| Neighbourhood Income and Demographics | 13C0015 | Spring - Summer |
| Economic Dependency Profile | 13C0017 | Spring - Summer |
| Labour Income Profile | 71C0018 | Spring - Summer |
| Families | 13C0016 | Spring - Summer |
| Seniors | 89C0022 | Spring - Summer |